Private Endpoints for Azure SQL Servers
In the era of cloud-first strategies, data security and network isolation have become more critical than ever. One powerful feature in Microsoft Azure that helps organizations achieve tighter security around their data assets is Private Endpoints—especially when it comes to securing Azure SQL Databases and Managed Instances.
In this blog post, we’ll explore what private endpoints are and their practical use cases, and how they ultimately enhance security for Azure SQL environments.
What Are Private Endpoints?
A Private Endpoint in Azure is a network interface that connects you privately and securely to a service powered by Azure Private Link. When used with Azure SQL Server, it allows you to access your SQL database through a private IP address from within your virtual network (VNet), effectively bypassing public internet access.
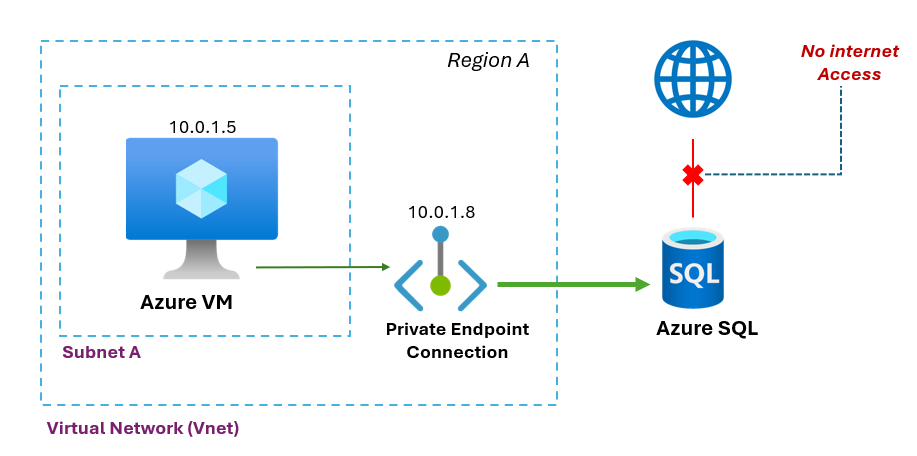
Hence, we can protect our Azure SQL Database without using a public endpoint and without traffic routed to Internet.
An Azure Private Endpoint is a network interface that provides secure, private connectivity to services using Azure Private Link. It assigns a private IP address from your virtual network (VNet), making the service accessible as if it were part of your VNet. All traffic between your VNet and the service remains on the Microsoft backbone network, eliminating the need to expose the service to the public internet.
The diagram below only illustrates that the private endpoint created for the SQL Database is accessible from an Azure Virtual Machine within the same virtual network.
However, Azure Private Endpoints can be accessed in several ways. These include from a peered virtual network within the same region, or through a virtual network–to–virtual network connection across regions. Additionally, clients can connect from on-premises environments using ExpressRoute with private peering or through a VPN tunnel.
Things you should note:
* When creating a Private Link Service, a network interface is created for the life-cycle of the resource and the interface is not manageable by user.
* The Private Link Service must be deployed in the same region as the virtual network.
* A single Private Link Service can be accessed from multiple Private Endpoints belonging to different VNets, subscriptions and/or Entra tenants.
Some Use Cases for Private Endpoints with Azure SQL
1. Isolated Access from On-Premises Networks
Organizations can use a VPN or ExpressRoute to extend their on-premises networks to Azure. By using private endpoints, they ensure that traffic to Azure SQL databases remains on a private network path—never touching the public internet.
2. Secure Access from Azure Virtual Machines or App Services
If your application runs on an Azure VM, App Service Environment (ASE), or Kubernetes cluster, a private endpoint allows those workloads to connect to Azure SQL databases securely without needing public IPs.
3. Multi-Tenant SaaS Scenarios
For SaaS providers managing tenant-specific databases, private endpoints offer a secure and isolated way to allow tenants to access their databases without exposing shared infrastructure.
4. Regulatory and Compliance Requirements
In industries like finance or healthcare, data access over public endpoints might violate compliance. Private endpoints provide the needed network-level isolation to satisfy these requirements.
Security Enhancements Enabled by Private Endpoints
End-to-End Private Connectivity
All traffic between your application and the SQL database traverses the Microsoft backbone network rather than the public internet, dramatically reducing the risk of data interception.
Granular Access Control
You can use Network Security Groups (NSGs) and Azure Role-Based Access Control (RBAC) to tightly control which subnets and users can interact with the private endpoint.
Integration with Azure Policies
You can enforce policies to ensure that only private endpoints are used to access certain data resources, adding a governance layer.
Defense Against Data Exfiltration
Since private endpoints are mapped to specific resources, the possibility of connecting to unauthorized services from within a VNet is minimized.
Final Thoughts
Private Endpoints for Azure SQL are a game-changer for organizations prioritizing security, compliance, and network isolation. While they require thoughtful planning and DNS configuration, the benefits in terms of risk mitigation and data protection are significant.
As cloud architectures continue to evolve, integrating services like Azure SQL with Private Link ensures you’re not only taking advantage of Azure’s scalability and flexibility but doing so without compromising on security.
“IntelliOpz can assist you with implementing Azure SQL private Endpoints – Feel free to get in touch”.

